Android PentesterLab06 - Reverse Engineering apk application | Shahul Hameed
How to reverse engineering in Android application
Required tools :
1. JAD ()
2. DEX2JAR ()
3. 7ZIP
Note: Put your apk app and all tools in a single folder(to easy
access).
Step 1: To redirect the command prompt directly.
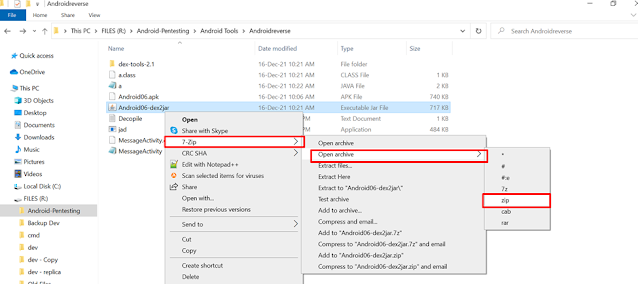
Step 2: Convert DEX to JAR
Using tool dex2jar
Now we got extracted file
Step 3: We extracted the jar file
Using the 7Zip tool
Choose your required files and copy them to your local disk.
Now we got Class files but we can’t edit them so next, we have to convert the Class file into Java.
Using a tool: JAD
Step 4:
Convert class file to java file
Use any online java compiler to execute the below code.
Note: Take the secret key from a.java and MessageActivity.java source code.
import java.util.Base64;
import javax.crypto.Cipher;
import
javax.crypto.spec.IvParameterSpec;
import javax.crypto.spec.SecretKeySpec;
public class Main
{
public static void main(String[] args) {
try
{
String s
="ygiG2VpgnW6z2ocCPEVaYhDwBs3UxZENbgh1iQJ6NhpBqHsczQsDh1rD3WjejQ7JH1o+lvBdtxhG64qyLQyHSg";
String key = "__pentesterlab__";
byte abyte1[] =
Base64.getDecoder().decode(s);
byte iv[] = new byte[16];
System.arraycopy(abyte1, 0, iv, 0,
16);
IvParameterSpec ivparameterspec = new
IvParameterSpec(iv);
int z = abyte1.length - 16;
byte enc[] = new byte[z];
System.arraycopy(abyte1, 16, enc,
0, z);
SecretKeySpec skey = new
SecretKeySpec(key.getBytes(), "AES");
Cipher cipher =
Cipher.getInstance("AES/CBC/PKCS5Padding");
cipher.init(2,skey,
ivparameterspec);
String res = new
String(cipher.doFinal(enc));
System.out.println(res);
}
// Misplaced declaration of an
exception variable
catch(Exception e)
{
e.printStackTrace();
}
}
}
Step 5: Finally, we got the key.










Comments
Post a Comment