Directory Enumeration | Shahul Hameed
Download Paths:
1. https://github.com/danielmiessler/SecLists
2. https://github.com/trickest/wordlists
GoBuster:
Installation : sudo apt install gobuster
Help: gobuster -h
Run : gobuster dir -u http://testphp.vulnweb.com -w /usr/share/wordlists/dirbuster/directory-medium-2.3.txt
If you want to list directories and its content based upon certain extensions like .txt, .css, .js etc. for that you can use the -x flag
gobuster dir -u http://testphp.vulnweb.com -w /usr/share/wordlists/dirbuster/directory-medium-2.3.txt -x .txt,html,css,js
Dirb
dirb http://testphp.vulnweb.com /usr/share/wordlists/dirb/common.txt
Dirbuster
Dirbuster
Now we’ll use Dirbuster — A GUI version of dirb to enumerate the directories.
Go to the Application icon -> Web Application Analysis -> Web crawlers and Directory Bruteforce -> Dirbuster

Now enter the target information and the wordlist file step wise as shown in the image below.

After the information has been filled, click on Start button to start the attack. The window will look like this.
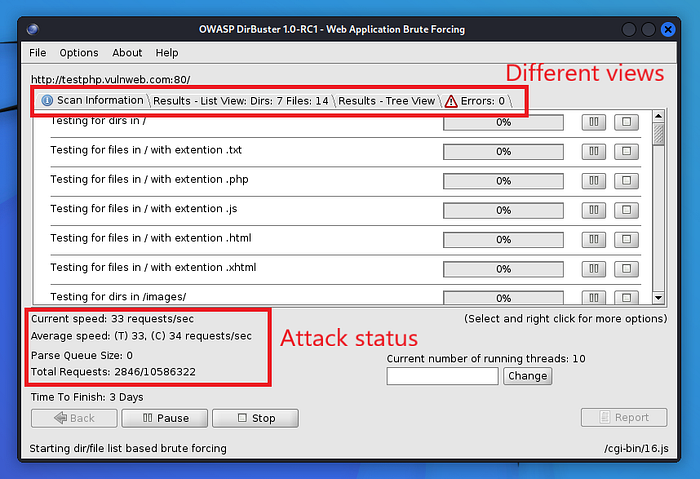
Let’s switch to List view and Tree view to view the results.

The above image is of the list view of the directories that have been found in the webserver. We can right-click on the interested file and will get several options like Open in Browser etc.
Let’s explore the tree view.

Like the list view, we can right-click and can get several options like View Response which will show us the HTTP Response of the website.
These were the 3 easy and most used methods of enumerating directories on a vulnerable web application. This is all for today. See you at the next one :)



Comments
Post a Comment